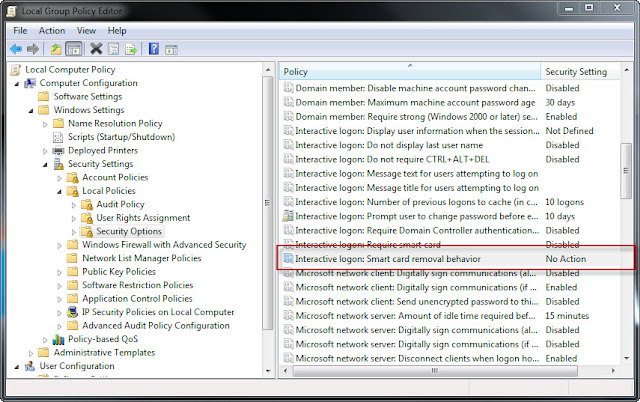
- Do nothing (default)
- Lock workstation
- Force Log-off
- Disconnect if a Remote Desktop Services connection.
Microsoft changed the way it handles Smart Card removal in Windows 7. They introduced a "Smart Card Removal Policy" service that must be running for this to work. By default this service is configured to start up manually. To test this locally, open up the Services console (services.msc),find the "Smart Card Removal Policy" service, and change the start up type to "automatic" and start the service.
Next, modify the Local Group Policy for your computer.
- Open gpedit.msc
- Expand Computer Configuration --> Windows Settings --> Security Settings --> Local Policies --> Security Options.
- Edit the "Interactive logon: Smart card removal behavior" policy to perform the desired action.
That is all there is to it! Of course you will need to configure the Domain Policy to push these changes out to all of your users!